Despite the increase of cyber-attacks across all types of organizations and the U.S. Government, many entities still do not have adequate controls in place to prevent data breaches or the means to detect them when they have occurred. Given the sophistication of the most recent attacks, many organizations lack effective tools to even determine if a breach has occurred and what the impact may be to customers.
The recent U.S. National Security Breach (identified in December 2020) will highlight and exasperate many shortcomings. For those in the Financial Services industry, it is imperative that all entities quickly determine: if a breach occurred (even if no initial and obvious signs of a breach are present); the extent of exposure; exposed gaps and weaknesses; and the extent of identified vulnerabilities. Notification of any breaches should be made to the appropriate regulatory bodies and to affected customers as soon as possible.

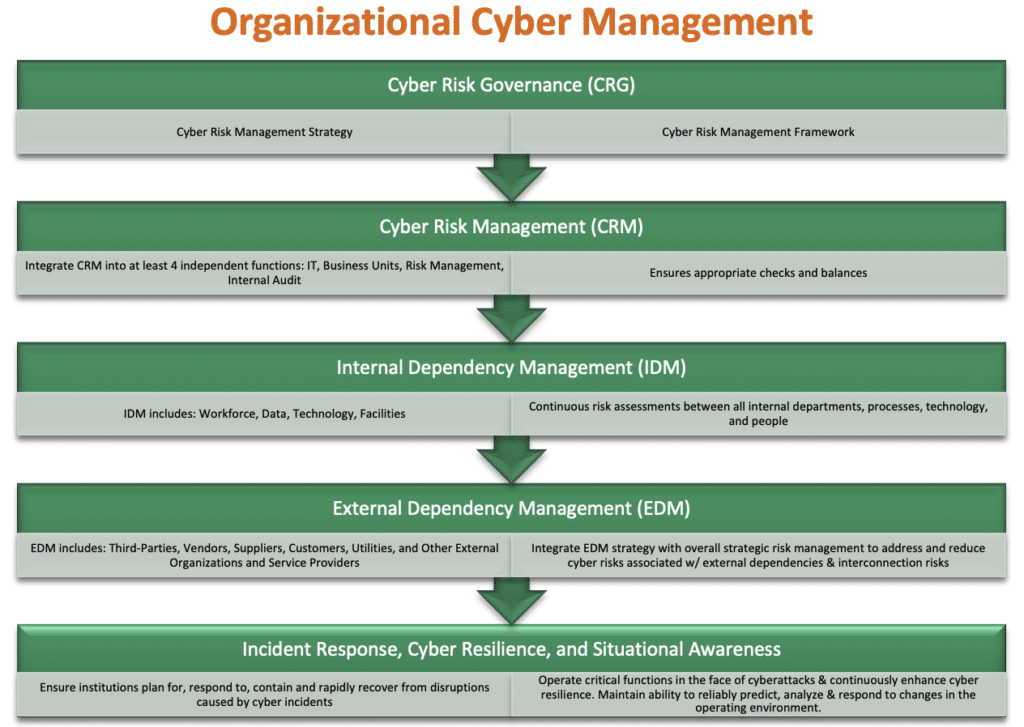
Without a doubt, cybersecurity and the recent national attacks are of the utmost concern for all CISO's in all industries. Many financial institutions are re-examining their Cybersecurity Corporate Governance programs in line with regulatory guidance:
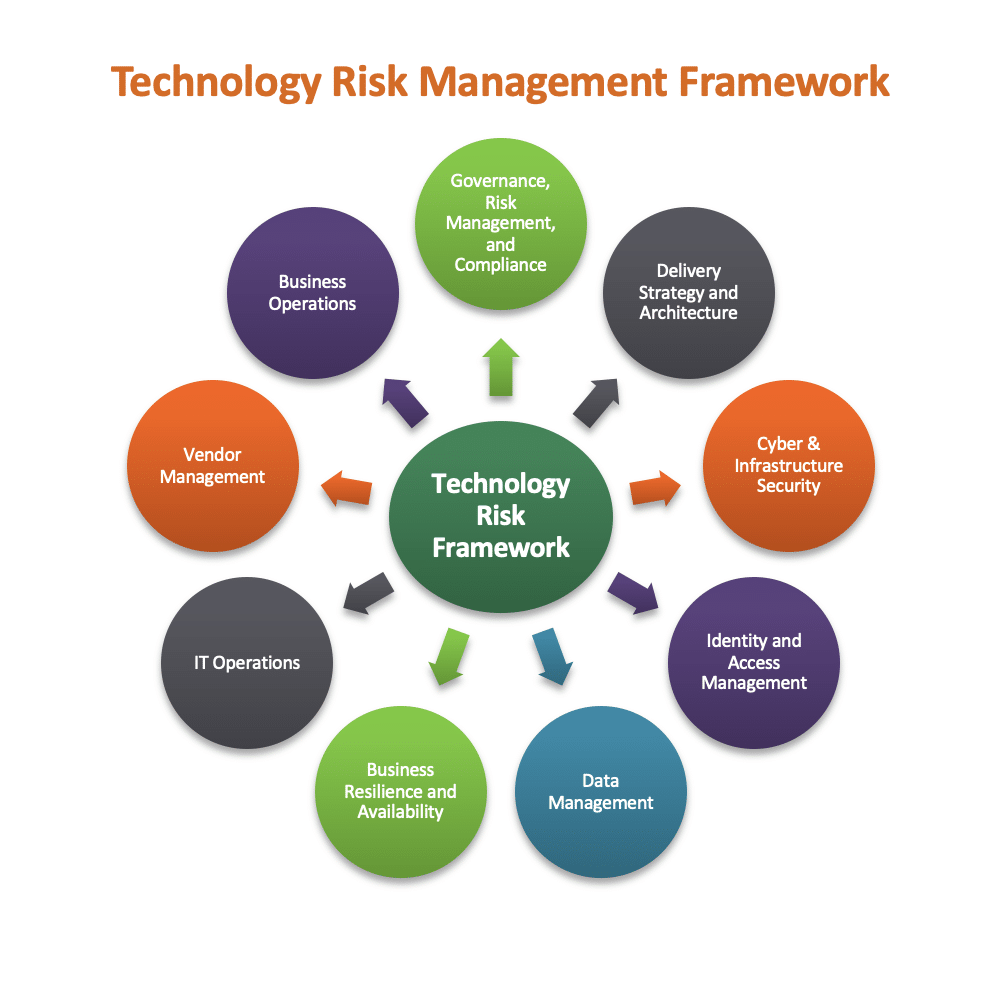
Additionally, financial services companies are moving quickly to examine and reinforce all aspects of their Technology Risk Management Framework, including at a minimum each of the following components:
DIRECTIVES FROM THE REGULATORS:
I. National Banking Regulators: On December 18, 2020, just after the national governmental breach, the Federal Financial Regulatory Agencies announced a proposal that would require:
- Supervised banking organizations to promptly notify their primary regulator of a computer security incident that:
- Could result in a banking organization’s inability to deliver services to a material portion of its customer base
- Jeopardizes the viability of key operations of a banking organization
- Impacts the stability of the financial sector
2. Service Providers to notify affected banking organizations immediately when the service provider experiences computer Security Incidents that materially disrupt, degrade, or impair certain services they provide.
The proposed rule is intended to provide the agencies with an early warning of significant computer security incidents and would require notification as soon as possible and no later than 36 hours after a banking organization determines that an incident has occurred.
The proposal can be found here: https://www.occ.gov/news-issuances/news-releases/2020/nr-ia-2020-175.html?utm_source=dlvr.it&utm
II. FFIEC: Well before the recent national governmental breach, the U.S. Financial Services Regulatory Agencies had identified weaknesses in various technology infrastructures and risk management procedures within many of the largest banks in the U.S. during 2019 and 2020. In this regard, the FFIEC (OCC, FRB, FDIC, NCUA) issued a Joint Statement during the second quarter of 2020 regarding the use of cloud computing services and security risk management principles for the financial services sector. The statement does not contain new regulatory expectations, rather it:
1. Highlights examples of risk management practices for a financial institution’s safe and sound use of cloud computing services and safeguards to protect customers’ sensitive information from risks that pose potential consumer harm around:
- Risks associated with use of third parties in a cloud environment
- Risk management considerations around:
............Governance
............Cloud security management
............Change management
............ Audit and controls assessment
2. Contains supervisory perspectives on effective information technology risk management practices, as well as references to other resources such as the:
- National Institute of Standards and Technology
- National Security Agency
- Department of Homeland Security
- International Organization for Standardization
- Center for Internet Security
- Cloud Security Alliance
The Joint Statement can be found here: https://www.fdic.gov/news/financial-institution-letters/2020/fil20052.html
TRENDS FROM THE OFFICE OF THE COMPTROLLER OF THE CURRENCY'S REGULATORY EXAM FINDINGS:
Meanwhile, the OCC has heightened its focus on risks around cyber and information technology during their 2020 examinations of financial institutions. From those examinations, we have seen a sharp increase in the number of Consent Orders being issued by the OCC to some of the largest banks in the country. The chart below details common findings across the industry.
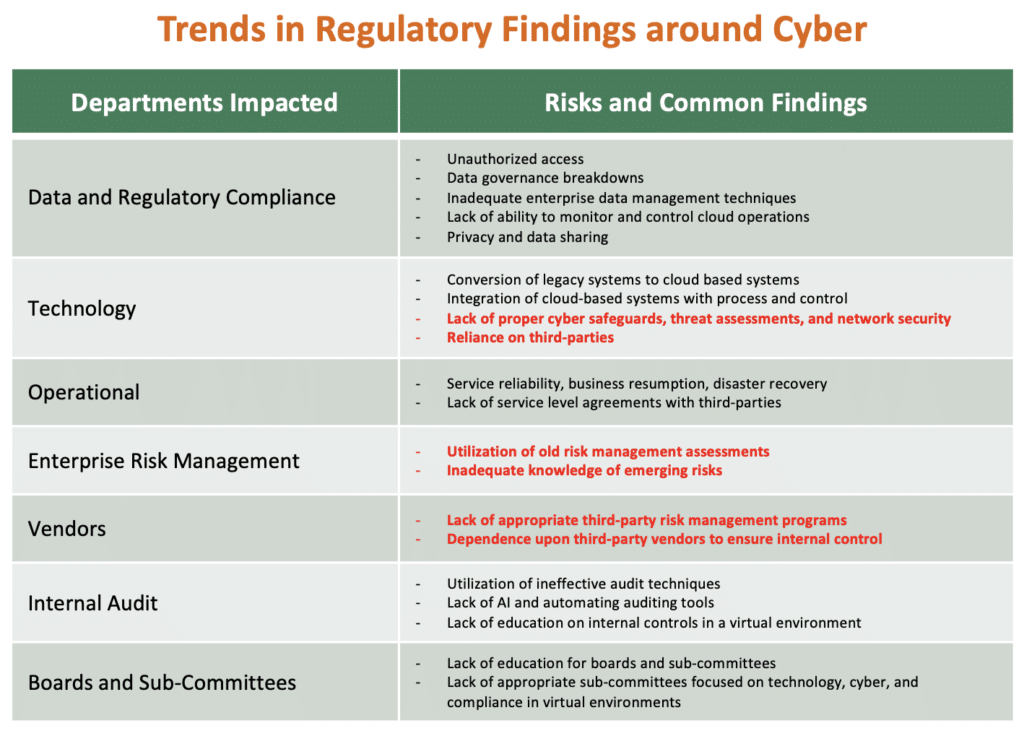
Continuous work and attention is required by all financial services companies to stay in front of cyber risk and to manage the ever-increasing sophistication of hackers today.
We expect that the U.S. Regulators may initiate a "Horizontal Review" in the coming months in regard to Cybersecurity at the largest financial institutions. Management should act now however, well in advance of such regulatory oversight.
IMMEDIATE ACTIONS TO CONSIDER:
In preparation for potential horizontal reviews, management should re-consider the following leading practices, among other things, in terms of cybersecurity, cyber-hygiene, and good cyber-governance:
1. Determine if a Breach Has Occurred
Security breach assessment and response often requires multiple areas/departments of the institution (information security, marketing, customer-facing departments, etc.) to react and work together, sometimes with great urgency. Compliance may be looked upon to lead or help:
- Assess whether the nature of the security incident requires: outside legal counsel to mitigate litigation risk; the advice of external consultants with expertise in that type of incident; and/or regulator notification.
- Ensure there is a detailed record built of the institution’s response actions and the evidence of system settings, detection logs, event logs, etc. are retained.
- Track and communicate developments internally to senior management and the board of directors.
- Evaluate the severity of any potential impact on the bank and its customers, including risk of identity theft.
- Identify affected systems, customers and plan public statements and/or customer communications.
- Serve as the communications liaison to external parties such as vendors, insurance companies, law enforcement and regulators.
In the case of a vendor breach, it may fall within the scope of compliance to:
- Communicate with the vendor to determine their incident response preparedness.
- Monitor the vendor’s execution of its incident response plan.
- Help evaluate the risk presented by the bank’s continued use of the vendor.
2. Assign Ownership
- Establish senior-level accountability for identifying data breaches, protecting customer/client data, and ensuring good corporate hygiene around broader data governance arrangements.
- Ensure that roles and responsibilities relating to data stewardship and protection are well defined.
- Introduce a privacy-by-design approach to systems acquisition and design.
3. Identify Risks
- Define what constitutes personal and sensitive data in the context of the organization and firmly establish the organization’s risk appetite for data loss.
- Ensure that privacy impact analysis is intrinsic to project methodology.
- Maintain logical data mapping of key flows of personal information.
- Consider adopting an ongoing cycle of automated data discovery and classification of new and existing data assets.
4. Protect
- Establish appropriate information security controls, including policies, procedures, and technical and human resources controls, to protect data assets adequately.
- Review and extend existing privacy policy and procedures.
- Evaluate and implement appropriate privacy- enhancing technologies to secure personal information (e.g., access control, intrusion detection and data encryption).
- Enhance the privacy culture by ensuring that staff receive training and awareness in recognizing suspicious activities that could indicate attempts to gain unauthorized access to sensitive data.
5. Respond
- Ensure existing cyber-incident response and breach investigation capabilities can meet the requirements of all laws, regulations, and prudent standards of good corporate governance...including the ability to perform an impact assessment, take remediation steps and honor consumer notification periods.
- Ensure that cyber-defense procedures are incorporated into the organization’s overall recovery plan.
- Consider whether to activate a cyber-insurance policy, and how to decide whether to notify customers of a cyberattack.
- Test response plans immediately to make sure everyone understands their roles and they can meet the required timelines.
FINAL THOUGHTS:
The General Data Protection Regulation from the European Union, along with a multitude of U.S. Federal Regulations, and a slew of State Regulations (such as the California Consumer Protection Act) will impact a much larger number of organizations than just financial institutions. Broader consequences for data governance and security are included in those laws and include far stiffer sanctions for non-compliance. Anyone who captures or processes personally identifiable information has a responsibility to act under the law.
Please reach out to me directly to discuss in more detail and how I may help you assess and remediate your particular situation. Our team is prepared to assist our clients on any element of their cybersecurity program requirements across an array of industries.
The views reflected in this article are my own and do not necessarily reflect the views of Cherry Bekaert.
Sources and Credits: FFIEC, OCC, FRB, FDIC, American Bankers Association, ABA Risk & Compliance, Crowe, Protiviti, SM+Co, Cherry Bekaert


